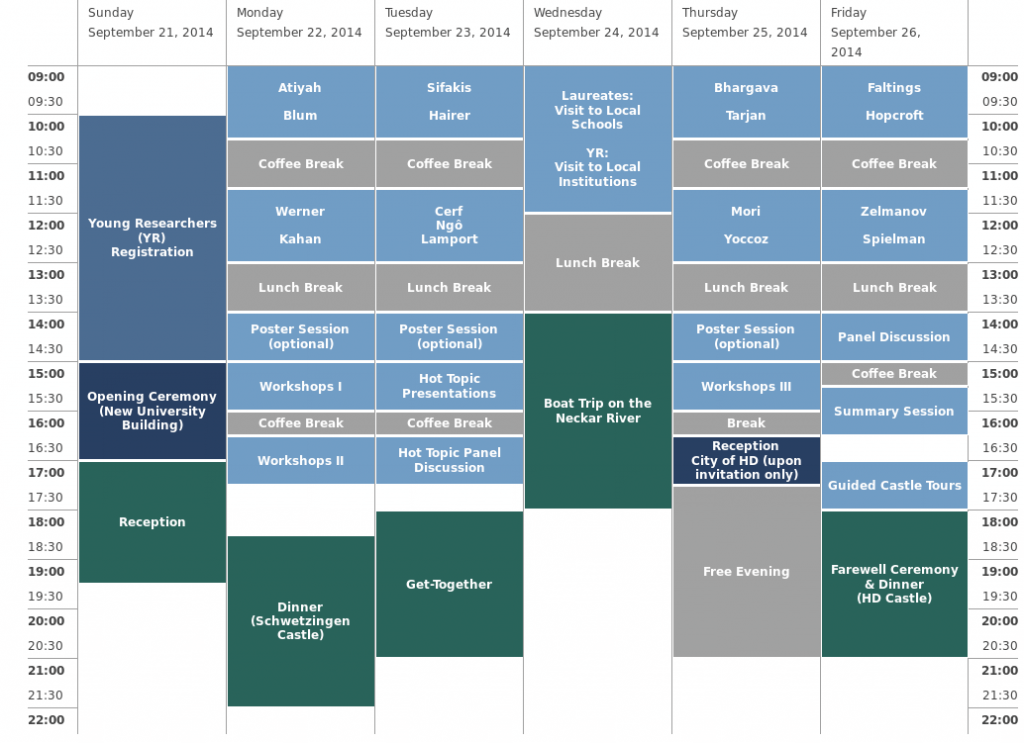
Shellshock είναι το όνομα που δόθηκε σε μια ευπάθεια που υπάρχει στο GNU Bash και αφορά τις εκδόσεις 1.14 έως 4.3. H ευπάθεια επιτρέπει ενδεχομένως σε κακόβουλους χρήστες να πάρουν τον έλεγχο του συστήματος ή/και να πραγματοποιήσουν απομακρυσμένη εκτέλεση αυθαίρετου κώδικα απευθείας στο ευάλωτο σύστημα.
Δεδομένης της ευρείας χρήσεως του λογισμικού GNU Bash σε λειτουργικά συστήματα GNU Linux / Unix / Mac OS / Windows / Android ο αριθμός των δυνητικά ευάλωτων συστημάτων εκτιμάται ότι αγγίζει αρκετά εκατομμύρια συστήματα. Οι εκδόσεις 1.14 έως 4.3 του GNU Bash καλύπτουν 25 χρόνια εγκαταστάσεων του εν λόγω λογισμικού!
Σύμφωνα με τις τελευταίες εκτιμήσεις οι επιθέσεις που ήδη έχουν εκδηλωθεί και αφορούν στην ευπάθεια Shellshock έχουν ξεπεράσει το ένα δισεκατομμύριο .
O οργανισμός NIST έχει βαθμολογήσει την ευπάθεια Shellshock ως 10 από 10 σε όρους της σοβαρότητας, των επιπτώσεων και της δυνατότητας αξιοποίησης. Επιδεινώνοντας το πρόβλημα, η ευπάθεια Shellshock επίσης κατατάσσεται χαμηλά στην κλίμακα της πολυπλοκότητας, το οποίο σημαίνει ότι έχει τη δυνατότητα να χρησιμοποιηθεί εύκολα από ένα μεγάλο ποσοστό κακόβουλων χρηστών (script kiddies).
Συνολικά αναγνωρίστηκαν 6 διαφορετικά bugs στο λογισμικό GNU Bash τα οποία αντιμετωπίστηκαν. Αναλυτική χρονική περιγραφή μπορείτε να δείτε εδώ.
Περιγραφή
Το λογισμικό GNU Bash απο την έκδοση 1.14 μέχρι την έκδοση 4.3 συνεχίζει να επεξεργάζεται τα ακολουθούντα αλφαριθμητικά μετά τις δηλώσεις συναρτήσεων στις τιμές των μεταβλητών περιβάλλοντος, επιτρέποντας σε απομακρυσμένους επιτιθέμενους να εκτελέσουν αυθαίρετο κώδικα, όπως αποδείχθηκε στις περιπτώσεις που αφορούν την ιδιότητα ForceCommand στο λογισμικό OpenSSH sshd, το mod_cgi και mod_cgid modules στον Apache HTTP Server, scripts που εκτελέστηκαν από πελάτες DHCP , αλλά και άλλες περιπτώσεις όπου πραγματοποιείται ρύθμιση του περιβάλλοντος μέσω του Bash shell
Ιστορικό
Η ευπάθεια Shellchock ανακαλύφθηκε από τον Stéphane Chazelas, αναφέρθηκε στον προγραμματιστή του GNU Bash και της αποδόθηκε το αναγνωριστικό CVE CVE-2014-6271. Ωστόσο, στην αρχή το το πρόβλημα δεν έγινε πλήρως κατανοητό, και η λύση που παρουσιάστηκε δεν απαντούσε πλήρως στο πρόβλημα .
Το αναγνωριστικό CVE-2014-7169 έχει ανατεθεί για να καλύψει το θέμα ευπάθειας που εξακολουθούσε να υπάρχει μετά τη λανθασμένη διόρθωση.
Υπάρχει αποθετήριο κώδικα "proof of concept" της ευπάθειας Shellshock στο GitHub.
Έλεγχος
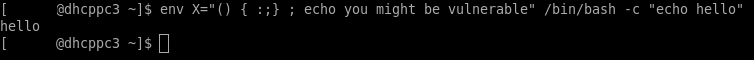
Μπορείτε γρήγορα να ελέγξετε την ευπάθεια του συστήματος σας εκτελώντας την παρακάτω εντολή στο GNU Bash :
env X="() { :;} ; echo you might be vulnerable" /bin/bash -c "echo hello"
Aν εμφανιστεί το μήνυμα “you might be vulnerable” τότε το σύστημα σας έχει εγκατεστημένη ευπαθή έκδοση του GNU Bash.
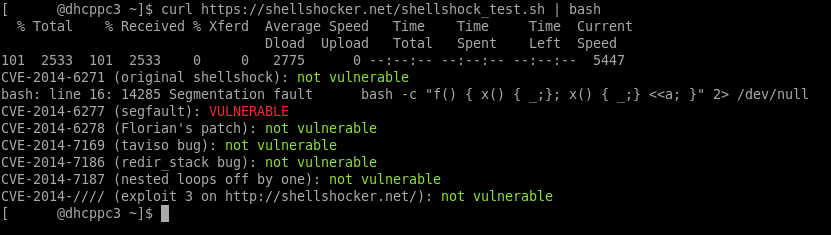
Εναλλακτικά μπορείτε να εκτελέσετε online έλεγχο του συστήματος σας στη διεύθυνση https://shellshocker.net/
Σχετικά
David A. Wheeler: Shellshock
Troy Hunt's Shellshock FAQ