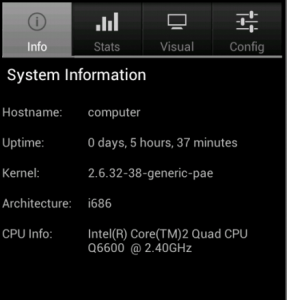
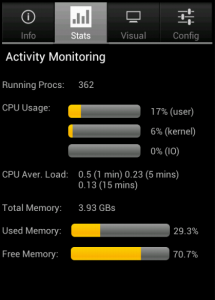
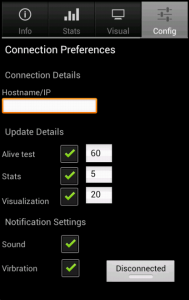
The attack is based on a 3-step methodology that can be fully automated in order to deploy massive attacks against vulnerable systems. The methodology takes advantage of the “Google Hacking” technique and extends it with two more steps that of information manipulation and the deployment of an exploit. Specially crafted implementations of the proposed attack methodology can be used per se to prevent cyber crime operations through the identification of vulnerable systems and prevention of massive cyber attacks against vulnerable systems.